Cybersecurity in Healthcare and its Challenges
From emergency surgeries to routine checkups, healthcare is something everyone depends on. As hospitals and clinics adopt more digital tools, the risk to cybersecurity in healthcare grows too. When systems are connected, attackers have more ways to get in—and the impact can be serious.
Why Healthcare Is a Major Target
Healthcare organizations hold data that is valuable to criminals and even nation-state actors. The AHA Center for Health Innovation, Innovation notes that healthcare organizations are heavily targeted because of the “high monetary and intelligence value” of the information they store.
Because of this, it’s worth asking two questions:
-
How does your provider protect your data?
-
How quickly can they respond if something goes wrong?
Current Threats to Cybersecurity in Healthcare
Healthcare data breaches generally fall into two categories: internal and external incidents.
Internal Data Breaches
Internal data breaches involve someone inside the organization or someone using internal access. Common examples include:
-
Unauthorized access or disclosure
-
Improper disposal of records
-
Loss or theft of devices or media
External Data Breaches
External data breaches are caused by outside actors. These often include:
-
Hacking or IT attacks
-
Spyware or malware
-
Phishing and credential theft
Although both types are damaging, the most frequent breach categories reported over the years include hacking/IT incidents, unauthorized access/disclosure, and loss/theft, as highlighted by HIPAA-related reporting.
Next, let’s look at major real-world cases to understand the scale of the problem.
Major Breach Examples in Healthcare
Hacking/IT
According to The HIPAA Journal, Change Healthcare Inc. had the most severe and widespread example of a Hacking/IT data breach, highlighting significant challenges of cybersecurity in healthcare. Change Healthcare experienced one of the most severe healthcare breaches, impacting around 190 million individuals in 2024.
The company reported a ransomware attack in late February. It later confirmed that data had been accessed over multiple days in February, and notifications were sent to affected individuals later in the year.
This case shows why ransomware is not only a data issue—it can become an operational crisis.

Unauthorized Access/Disclosure
Kaiser Foundation Health Plan reported a large breach affecting 13.4 million individuals in 2024. The organization stated that two workforce email accounts were accessed by an unauthorized party.
Even when emails are deleted and authorities are involved, sensitive information can still be exposed. In incidents like this, affected individuals are typically notified by email or mail.

Loss: SAIC / Tricare-Related Incident (2011)
Science Applications International Corporation (SAIC) experienced a loss-related breach in 2011 affecting 4.9 million people. Reports indicated that backup tapes were stolen from an employee’s car outside an SAIC facility.
Because backup media can contain large volumes of sensitive information, loss incidents like this can be extremely damaging—especially when encryption controls are weak or inconsistent.

Theft
Ranked at 19, Community Health Systems Professional Services Corporation had a theft data breach in 2014 affecting 4,500,000 individuals. According to The HIPAA Journal, “…the health system was hacked by a Chinese advanced persistent threat group which installed malware on its systems that was used to steal data.”
This is where consequences expand beyond IT. Costs can include legal exposure, regulatory penalties, and long-term reputational damage.

Regulatory Framework and Compliances
Healthcare organizations must follow strict regulations to continue operating safely and ethically.
Wake Forest university describes healthcare compliance as the effort to follow laws and internal standards to prevent fraud, abuse, and misconduct in the healthcare industry. In practice, compliance is also a security driver because it forces stronger controls around access, privacy, and incident response.
The Health Insurance Portability and Accountability Act of 1996 (HIPAA) “establishes federal standards protecting sensitive health information from disclosure without the patient’s consent.” This act consists of both Privacy and Security Rules. Under the Privacy Rule HIPAA covers healthcare providers, health plans, healthcare clearinghouses, and business associates. Meanwhile under its Security Rule, (HIPAA) “..protects a subset of information covered by the Privacy Rule. This subset is all individually identifiable health information a covered entity creates, receives, maintains, or transmits in electronic form.”
The Physician Referral Law (Stark Law)“prohibits physicians from referring patients to receive “designated health services” payable by Medicare or Medicaid from entities with which the physician or an immediate family member has a financial relationship, unless an exception applies.” Since the Stark law is a strict liability statute, it doesn’t require proof of specific intent to violate the law. However, violation of this law includes fines and “exclusion from participation in the Federal healthcare programs.”
The False Claims Act “a federal statute originally enacted in 1863 in response to defense contractor fraud during the American Civil War.” For any person who submits a false claim knowingly to the federal government is liable for “three times the government’s damages plus a penalty that is linked to inflation.” Additionally, under the qui tam suits, “the FCA allows private citizens to file suits on behalf of the government.”
The Anti-Kickback Statute (AKS) is a criminal charge that “prohibits the knowing and willful payment of “remuneration” to induce or reward patient referrals or the generation of business involving any item or service payable by the Federal health care programs.” “The statute covers the payers of kickbacks-those who offer or pay remuneration- as well as the recipients of kickbacks-those who solicit or receive remuneration.”
The Patient Safety Act “amended Title IX of the Public Health Service Act to provide for the improvement of patient safety and to reduce the incidence of events that adversely affect patient safety by authorizing the creation of patient safety organizations (PSOs). PSOs work with providers to improve quality and safety through the collection and analysis of aggregated, confidential data on patient safety events.”
Violations and Penalties
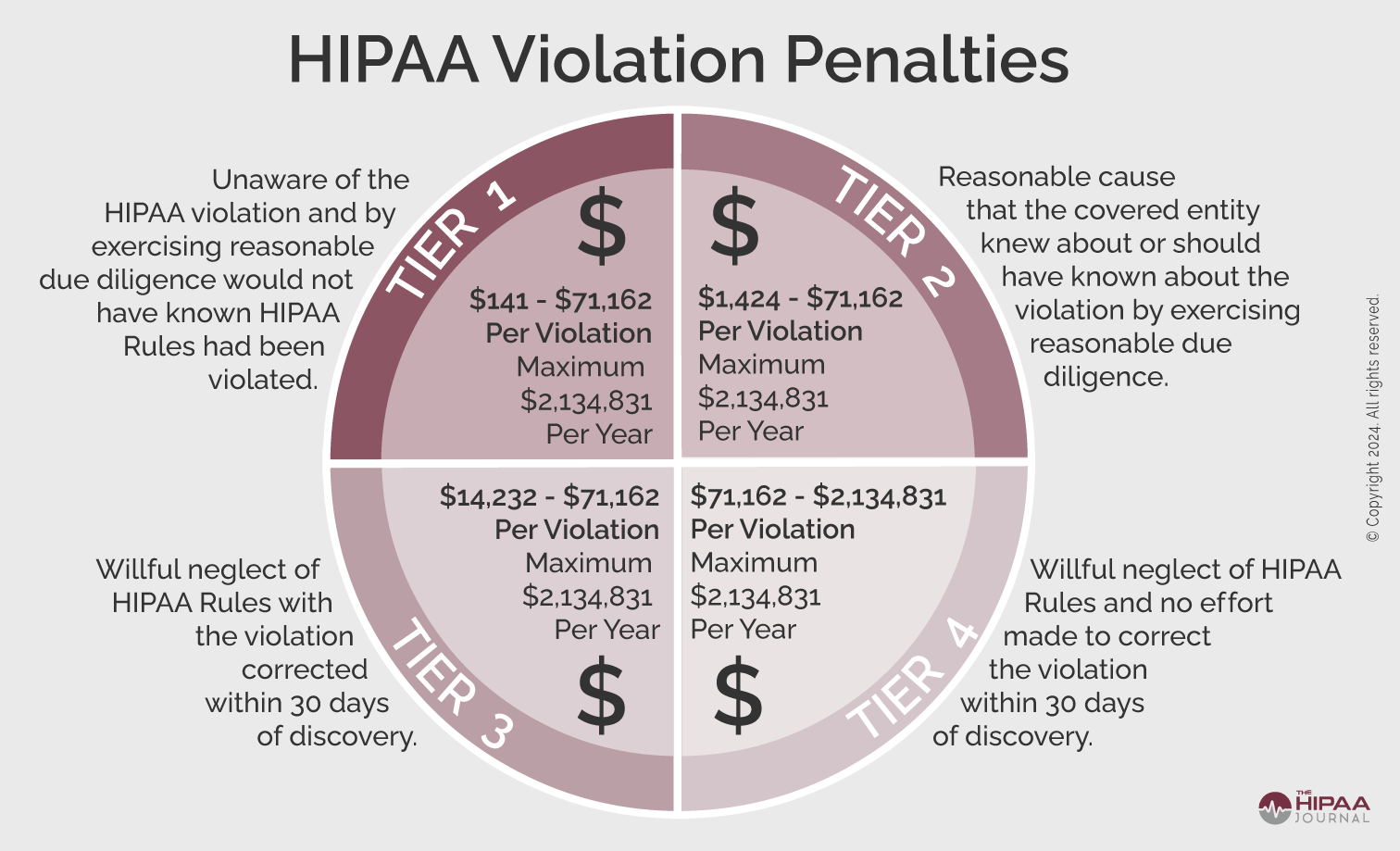
In addition to the strict rules are the strict penalties that follow them. Consequentially, this forces companies to act accordingly to prevent such violations from ever occurring. Specifically, in regard to HIPAA, as seen below, they have magnitudes to their violation penalties. Ranging from Tier 1, showcasing the punishments of unknowingly breaking the rules to Tier 4 where there was willful neglect and no attempts at prevention.
Solutions for Cybersecurity in Healthcare
No organization is completely immune to cyberattacks. However, preparation drastically reduces damage.
A strong approach starts with awareness:
-
What threats are most likely for your organization?
-
Where is your biggest exposure?
-
Which systems contain the highest-risk data?
When you know the answers, you can prioritize defenses instead of guessing.
(For more information and tips on cybersecurity in Health care click on here.)
While there are many problems within the technical aspect, sometimes the user can become their own demise too. Due to faster advancements, it’s natural for anyone to not completely understand the functions of an IoT device or its programs. However, this only leads us to be more susceptible to cyber-attacks. Therefore, understanding and maintaining a culture around one’s security can be pivotal to their success in safety. Due to this, it’s suggested that:
-
- Education and training must be a recurring effort one takes.
- By being self-regulated, this sets those as the standard of how one should act or think, especially in a managerial or leadership position
- Centering the organization’s core values around accountability and responsibility could promote trust and growth amongst its workforces.
“A firewall can take the form of a software product or a hardware device. In either case, its job is to inspect all messages coming into the system from the outside…and decide, according to pre-determined criteria, whether the message should be allowed in.” Therefore, by setting up a firewall companies will be able to track and view the programs an employee downloads and have the system determine whether the application or service is appropriate or not.
In turn, from scanning these applications firewalls can slow down, stop, and even report the downloads if deemed “rouge/unapproved”. While firewalls can be simplistic, it’s also important for a company to speak with their IT team or other resources to “…perform malware, vulnerability, configuration, and other security audits on a regular basis.”
The difference between firewalls and an anti-virus software is that a firewall prevents intruders from entering, while the software deals with the intruders that managed to enter. As for viruses, they can come into many shapes in sizes from an unassuming website download and emails to flash drives and even CDs. Henceforth, this it’s important to maintain updates on your IoT devices and use anti-virus software to regularly check up on your devices. Luckily, anti-virus software is well tested and widely available, having a range of prices, many of which are affordable for individuals and companies alike.
Signs that your device may have a virus:
-
- System will not start normally (e.g., “blue screen of death”)
-
- System repeatedly crashes for no obvious reason
-
- Internet browser goes to unwanted web pages
-
- Anti-virus software does not appear to be working
-
- Many unwanted advertisements pop up on the screen
- The user cannot control the mouse/pointere
While there are many technical threats that can compromise your data security, there are also many unexpected external factors that can affect you as well. Unfortunately, natural disasters of any kind can unexpectedly appear in one’s daily life. Due to this it’s important to not only create a backup but have a sound recovery plan. Firstly, when creating a backup, it’s easier to start it the very first day. By continuously updating and ensuring that the information is not only accurate but can be properly restored, provides companies and individuals a safety measure for the unexpected.
Additionally, it’s also important to keep storage devices containing the backups (such as hard drives, CDs, and DVDs) in a safe location where it wouldn’t be affected by the elements. Furthermore, scanning and uploading physical documents to these devices can also prove to be efficient and useful in the instance that the physical copy gets damaged. Using cloud computing can also be efficient and convenient due to its little use in technical expertise and nonphysical form. However, one must still be cautious when uploading backup files, so that they’re as secured as the original.
Actions and Improvements for Cybersecurity in Healthcare
Healthcare breaches are persistent, but that doesn’t mean progress is impossible. Security improves through consistent upgrades, better training, and smarter planning.
Even with reductions reported in some periods, healthcare continues to rank among the costliest industries for breaches. That reality makes prevention worth the effort.
Ultimately, patients should understand their rights and be careful with where they share data. Meanwhile, organizations should treat cybersecurity as part of trust and service quality—not only a compliance requirement.
When healthcare providers invest in security, they don’t just reduce risk. They also build credibility, strengthen loyalty, and protect long-term operations. (The HIPAA Journal)

Ultimately, understanding your rights and protections can improve your chances of securing compensation when data breaches occur. Staying vigilant about how and where you share your information also reduces the risk of future incidents, especially as concerns around cybersecurity in healthcare continue to rise.
For healthcare organizations, prioritizing cybersecurity in healthcare isn’t just about compliance, it’s about protecting patient trust. A strong commitment to cybersecurity in healthcare can differentiate providers from competitors and attract loyal patients, making the investment worthwhile.
SHARE ME!
MORE ARTICLES