The conversation in the enterprise world has fundamentally changed. As we analyze the emerging technology trends 2026, the digital transformation mandate moves past simple digitalization; it demands the creation of intelligent, self-managing, and geopolitically resilient enterprise architectures. Incremental fixes are no longer enough.
Gartner’s latest strategic technology trends 2026 confirm that this new era requires a profound architectural reset. We are moving from managing fixed processes to governing intelligent, self-directed systems, and from trusting global cloud providers to demanding data sovereignty.
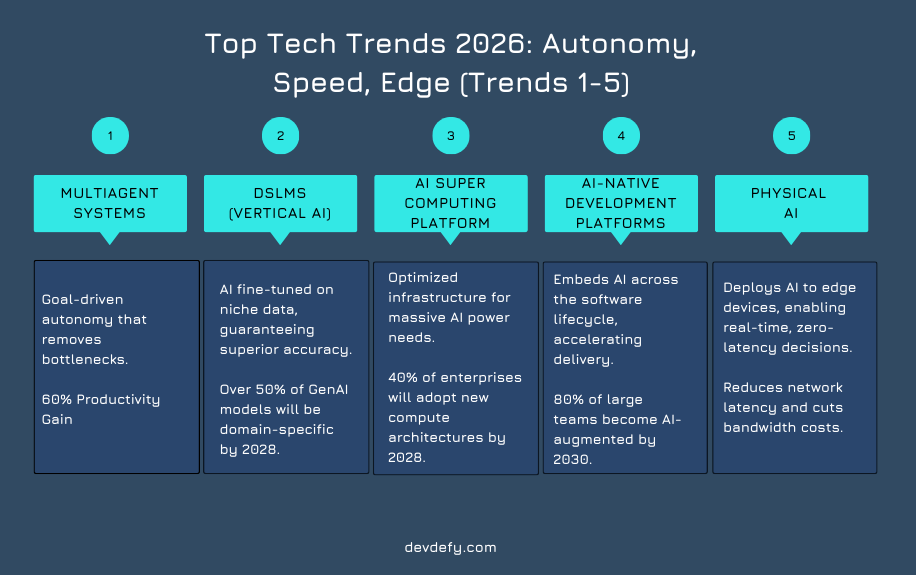
MAS eliminates the “human approval” delays that bottleneck systems like ERP and CRM. Early adopters report massive efficiency gains, with some seeing 60% productivity increases and faster decision-making.
Autonomy requires control. You must implement strong governance through Retrieval-Augmented Generation (RAG) systems to ground agents in your proprietary data, preventing ‘hallucination’ and ensuring policy alignment.
DSLMs deliver superior accuracy because they inherently understand industry jargon, eliminating the need for elaborate user prompts.
Gartner predicts that by 2028, over half of Generative AI models used by enterprises will be domain specific. This specialization provides a defensible competitive advantage.
You can design specialized AI models to provide medical or legal advice strictly grounded in proprietary protocols, guaranteeing high compliance and accuracy, or train proprietary ML Models to predict equipment failures with far higher precision than general models.
Success hinges on curating high-quality, domain-specific data. Partner with experts for ML Model Development to fine-tune open-source models or train a new proprietary model from scratch, ensuring scalability and performance for your niche needs.
This trend represents a complete redesign of the server infrastructure, creating an AI-native platform optimized specifically for the colossal computational demands of training and running advanced AI models.
Traditional data centers are inefficient for AI workloads. This specialized infrastructure makes large-scale AI deployment feasible, especially as power demand becomes a primary constraint.
Gartner predicts that by 2028, over 40% of leading enterprises will adopt hybrid computing architectures into critical business workflows (up from 8%).
It provides the necessary computational backbone to run vast Multiagent Systems and execute resource-intensive tasks like molecular simulation and real-time risk modeling.

Preparing requires expert Cloud Services and Architecture Design to leverage hyper-scalable, large-scale cloud solutions, utilizing container orchestration (Kubernetes) and microservices architecture for guaranteed performance.
This platform delivers significant ROI by automating repetitive tasks, allowing human developers to focus on architectural design and problem-solving. Developers using AI report substantial efficiency gains, typically ranging from 10% to 25% in productivity.
Gartner predicts that by 2030, this will result in 80% of organizations evolving large software engineering teams into smaller, more nimble teams augmented by AI.
The speed of AI code generation must be matched by deployment capability. Implement robust DevOps practices using containerization (Docker) and orchestration (Kubernetes) for smooth, scalable CI/CD deployment, a core Custom Software Development expertise of DevDefy.
This requires deeply integrated IoT Development Services. Design containerized cloud solutions that are seamlessly compatible with distributed edge nodes, utilizing platforms like AWS IoT and protocols like MQTT/CoAP for low-bandwidth environments.
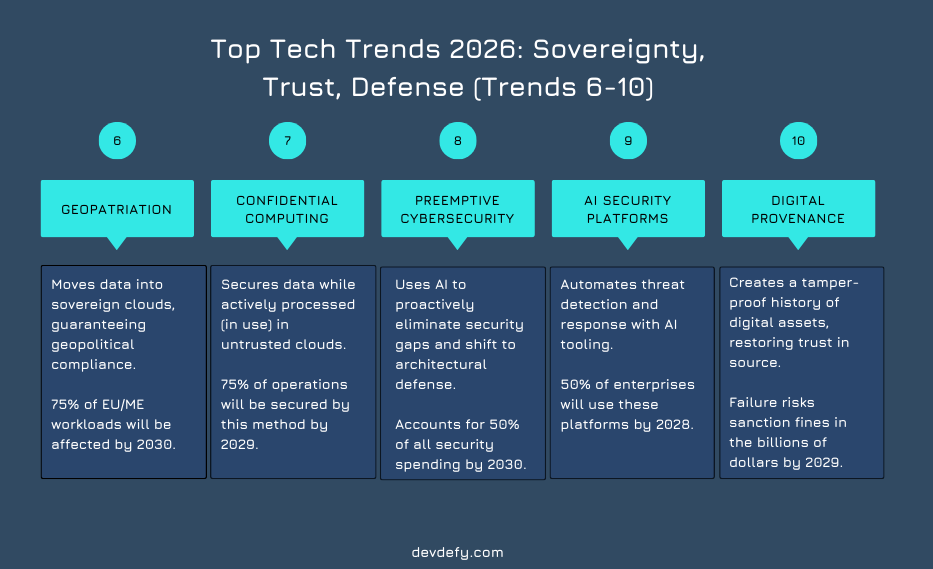
Leverage expert Cloud Services and Architecture Design to implement vendor-agnostic architecture. Use centralized key and access management (RBAC) and hybrid orchestration to enforce data boundaries and allow for seamless region and provider switching, guaranteeing geopolitical resilience.
Confidential Computing is a security framework that protects data while it is actively being used and processed by performing computation within a hardware-based, verified trusted execution environment (TEE).
Protecting data “at rest” and “in transit” is no longer enough. Confidential Computing aligns with the highest level of Zero-Trust Architecture (Verify Explicitly, Assume Breach) by strictly limiting the “blast radius” of any potential intrusion.
Gartner predicts that by 2029, more than 75% of operations processed in untrusted infrastructure will be secured in-use by confidential computing.
Allows companies to securely process highly sensitive information (e.g., patient records, financial data) using cloud-based AI/ML models without exposing the underlying data to the cloud provider itself. This is vital for regulated environments.
Implementation requires a complete shift to the Zero-Trust model. DevDefy’s Custom Software Development methodology ensures every application incorporates robust data encryption, secure access controls, and network segmentation into the initial design, utilizing specific TEE features offered by cloud providers for compliance.
Preemptive Cybersecurity moves security operations from a reactive, perimeter-based model to a proactive, foundational state. It uses AI and continuous verification to eliminate security gaps before they can be exploited.
Preemptive security builds trust and control into the development foundation, enabling rapid AI and cloud adoption because security is integrated and automated.
Gartner predicts that by 2030, preemptive solutions will account for half of all security spending, as CIOs shift from reactive defense to proactive protection.
Implement Security Implementation at every stage of the development lifecycle. This involves performing regular vulnerability assessments, threat modeling, and integrating robust data encryption and multi-factor authentication directly into the software’s foundational architecture.
These platforms provide a single, real-time, context-aware mapping of every data journey across code, infrastructure, SaaS, and AI systems, the foundational requirement for preemptive action.
Gartner predicts that by 2028, over 50% of enterprises will use AI security platforms to protect their AI investments.
The strategy requires a robust data foundation and the right tooling. DevDefy assists clients in integrating continuous monitoring and management practices (e.g., CloudWatch, Datadog) into the cloud deployment process to generate the necessary, high-quality operational data stream for effective AI Security Platforms.
In the age of generative AI and deepfakes, trust in data origin is collapsing. Digital Provenance restores that trust by providing cryptographic verification that ensures authenticity without intermediaries.
Gartner predicts that by 2029, those who failed to adequately invest in digital provenance capabilities will be open to sanction risks potentially running into the billions of dollars.
Critical for auditing compliance and ensuring the reliability of data used to train high-stakes Multiagent Systems and DSLMs. It’s used in supply chains to track high-value or ethically sourced products, verifying their authenticity.
Implementation relies on specialized Custom Software Development to integrate secure ledger systems or blockchain technologies with existing enterprise applications. Define the specific data points that require tracking, design the verification mechanism, and seamlessly integrate this trust layer into existing workflows.
The era of simple automation is over; the future demands a shift to deeply intelligent, self-managing systems. This paradigm shift is driven by the most critical technology trends 2026 has to offer, where AI moves from a passive assistant to an autonomous “agentic” workforce.
Achieving this enterprise autonomy requires a complete architectural reset: matching the massive speed of AI with robust, custom infrastructure, while ensuring security is built-in. This includes specifically addressing new geopolitical mandates for data control and continuous verification, core pillars of the technology trends 2026 landscape. Navigating this integrated, specialized transformation is complex.
Stop reacting to technological changes and partner with DevDefy today to transform these strategic imperatives into a custom, scalable, and resilient operational reality.
